Exploring the realm of cybersecurity habits for digital lifestyle unveils the critical practices needed to protect personal information in today's digital age. From password management to phishing awareness, this topic delves into the essential steps individuals must take to secure their online presence.
Highlighting the risks of cyber threats and the role of proactive security measures, this discussion sets the stage for understanding the importance of maintaining a secure digital lifestyle.
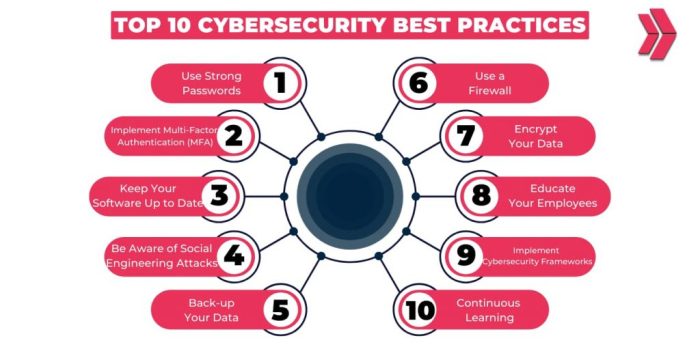
Top Cybersecurity Habits for Digital Lifestyle
In today's interconnected world, a digital lifestyle refers to the way individuals engage with technology on a daily basis, from online shopping and social media use to mobile banking and smart home devices.
It is crucial to adopt cybersecurity habits to safeguard personal information and protect against various online threats. By practicing good cybersecurity habits, individuals can reduce the risk of falling victim to cybercrimes like identity theft, phishing scams, and data breaches.
Importance of Cybersecurity Habits
- Use strong, unique passwords for each online account to prevent unauthorized access to personal information.
- Enable two-factor authentication whenever possible to add an extra layer of security to online accounts.
- Regularly update software and applications to patch vulnerabilities that cybercriminals could exploit.
- Avoid clicking on suspicious links or downloading attachments from unknown sources to prevent malware infections.
- Be cautious when sharing personal information online and limit the amount of data shared on social media platforms.
Risks of Neglecting Cybersecurity Practices
- Exposure to identity theft, where cybercriminals steal personal information to commit fraud or other crimes.
- Falling victim to phishing scams, where attackers trick individuals into revealing sensitive information like passwords or financial details.
- Data breaches that compromise sensitive data stored by online services, leading to potential financial loss or reputational damage.
- Ransomware attacks that encrypt files and demand payment in exchange for decryption keys, disrupting normal operations and causing financial harm.
- Unauthorized access to devices or accounts, allowing cybercriminals to spy on individuals, steal data, or engage in other malicious activities.
Individual Responsibility in Cybersecurity
- Stay informed about current cybersecurity threats and best practices to protect personal information.
- Educate family members or colleagues about cybersecurity risks and how to stay safe online.
- Report any suspicious activity or security incidents to the appropriate authorities or service providers.
- Backup important data regularly to prevent data loss in case of a cyber incident.
- Practice good digital hygiene by logging out of accounts when not in use and securing devices with strong passwords or biometric authentication.
Password Management
When it comes to cybersecurity, managing your passwords is crucial to keeping your online accounts safe from hackers and cyber threats.
Creating Strong, Unique Passwords
- Use a combination of uppercase and lowercase letters, numbers, and special characters to create complex passwords.
- Avoid using easily guessable information such as birthdays, names, or common words.
- Consider using passphrases, which are longer and easier to remember but still secure.
Using Password Managers
Password managers are tools that securely store and manage all your passwords in one place. They help generate strong, unique passwords for each account and can automatically fill them in when needed.
Regularly Updating and Changing Passwords
- Change your passwords regularly, ideally every 3-6 months, to reduce the risk of unauthorized access.
- Enable two-factor authentication (2FA) for an added layer of security on your accounts.
- Monitor your accounts for any suspicious activity and update passwords immediately if you suspect a breach.
Phishing Awareness

Phishing is a common type of cyber attack where malicious individuals attempt to trick people into revealing sensitive information such as usernames, passwords, and credit card details. It is prevalent in email, messaging platforms, and websites, posing a significant threat to individuals' cybersecurity.
Signs of Phishing Attempts
- Unsolicited emails requesting personal information or urgent action.
- Links or attachments from unknown senders or suspicious sources.
- Emails with poor grammar, spelling errors, or unusual sender addresses.
- Websites with misleading URLs or fake login pages.
Strategies for Verifying Communications
- Check the sender's email address for authenticity.
- Hover over links to see the actual URL before clicking.
- Verify requests for personal or financial information through other channels.
- Use security software to detect and block phishing attempts.
Avoiding Phishing Scams
- Avoid clicking on links or downloading attachments from unknown sources.
- Do not provide personal information in response to unsolicited requests.
- Be cautious of urgent or threatening messages that require immediate action.
- Report suspected phishing emails or websites to the appropriate authorities.
Software Updates and Patch Management
Keeping your software and devices up-to-date with the latest security patches is crucial in maintaining a secure digital environment. By regularly updating your systems, you can ensure that any vulnerabilities are patched, reducing the risk of cyber threats compromising your data.
Significance of Software Updates
- Software updates often include security patches that address known vulnerabilities.
- Updates can improve the overall performance and functionality of your devices and applications.
- Running outdated software puts your system at risk of exploitation by cybercriminals.
Tips for Enabling Automatic Updates
- Enable automatic updates for your operating system to ensure you receive the latest security patches.
- Set up automatic updates for applications such as web browsers, office suites, and other software to stay protected.
- Ensure your antivirus software is set to automatically update its virus definitions to detect and block new threats.
Role of Patch Management
- Timely patch management is essential in mitigating security vulnerabilities and reducing the attack surface of your systems.
- Regularly check for updates from software vendors and apply patches promptly to protect your devices.
- Implement a patch management strategy that includes testing patches before deployment to prevent any compatibility issues.
End of Discussion
In conclusion, adopting top cybersecurity habits for your digital lifestyle is not just a choice but a necessity in today's interconnected world. By following best practices in password management, staying vigilant against phishing attempts, and keeping software updated, individuals can significantly enhance their online security and privacy.
Stay safe, stay secure.
FAQs
How often should I update my passwords?
It is recommended to update your passwords at least every 3-6 months to reduce the risk of unauthorized access to your accounts.
What should I do if I suspect a phishing attempt?
If you suspect a phishing attempt, do not click on any links or provide any personal information. Instead, verify the sender's identity through other means and report the suspicious activity to the appropriate authorities.
Why are software updates important for cybersecurity?
Software updates often contain security patches that address vulnerabilities exploited by cyber threats. By keeping your software up-to-date, you can protect your devices from potential attacks.